Studies suggest that customers may be at risk from fake voice messages.
As voice messages become more popular as a form of communication between friends, family and colleagues, the threat of deepfakes and cybercrime also increases.
A 2024 survey conducted by Preply found that two-thirds of American adults have sent a voice message, while 41 percent admit to having seen an increase in voice message usage in recent years.
The popularity of voice notes coincides with a significant increase in deepfakes worldwide. A recent study shows that AI-powered audio and video fakes increased by 245 percent in 2024 compared to the previous year.
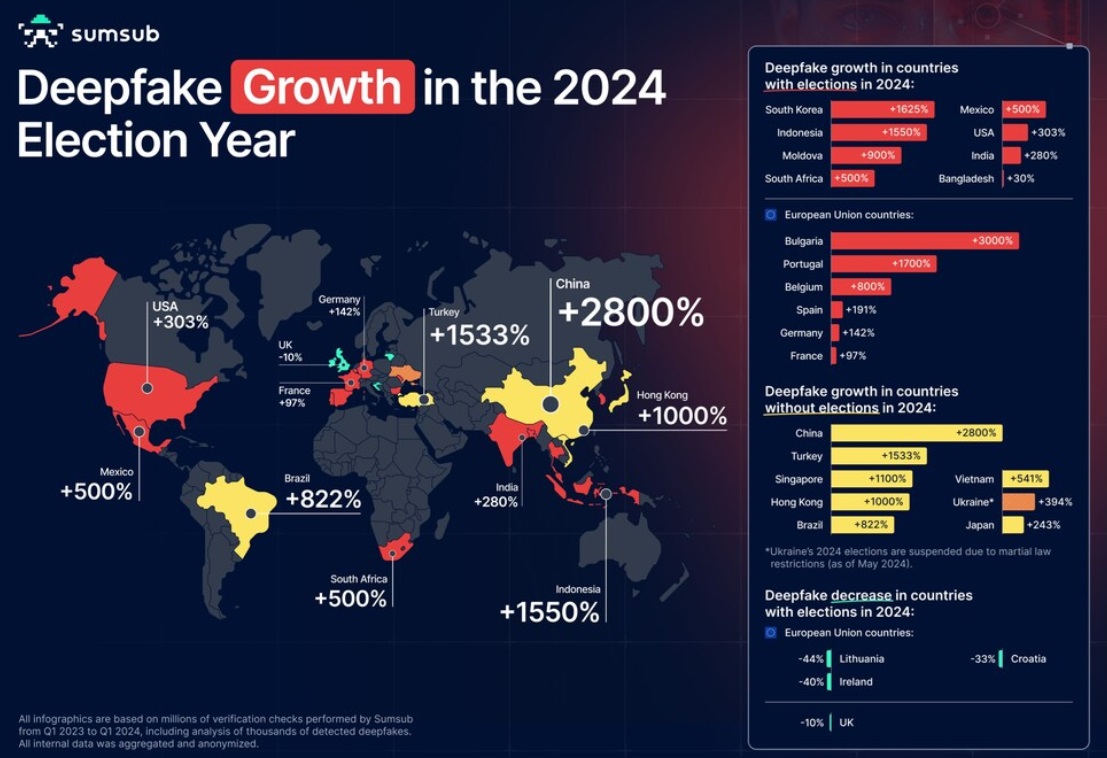
The countries most affected by deepfakes in the first quarter of 2024 include China, Germany, the US and the UK. And while the UK saw a 10 percent drop in actual fraud cases, this is not due to a lack of effort, as the number of detectable deepfakes still increased by 45 percent.
While the data does not distinguish between the number of audio and video deepfakes, Aaron Painter, CEO of the security solutions provider Name tagbelieves that the use of fraudulent audio data in cyberattacks is increasing:
“If you take over someone’s account, you can control everything that account has access to. For an employee account, that means you can inject ransomware or access sensitive company data.
To get a customer account, you could hijack social media or bank accounts. Deepfakes make this easier. They are superpowers for bad actors.
But how exactly do these criminals access and exploit customer voice recordings?
Audio deepfakes
Deepfake voice technology uses AI to clone a person’s voice, a feat that has become easier and more accurate thanks to advances in generative AI (GenAI).
With the increasing number of homemade videos on social media platforms such as Instagram, Facebook and TikTok, scammers can easily find and exploit people’s voice samples through simple online searches.
It is the proliferation and rapid development of AI tools that makes deepfake voice notes an easy and obvious choice for cyber fraudsters, Roman Zrazhevskiy, CEO of MIRA Safety.
Zrazhevskiy believes criminals will use this technology to trick people into revealing account passwords, credit cards and/or banking information. He explains:
“However, more sophisticated criminals will go deeper and will likely try to impersonate people close to you to create additional trust and urgency. Often, these schemes are aimed at extorting money or financial information.
However, we are also likely to see an increase in malware attacks, likely triggered by victims being tricked through their voice messages into downloading an app that they thought was recommended by a friend via voice message and followed by a direct link.
GenAI’s ability to imitate voices and manipulate unsuspecting people has even been discussed by its most famous proponent, OpenAI.
In an unauthorized blog posted on the company’s website in April, the company advised organizations to move away from voice authentication because of a new voice engine solution from OpenAI, a tool that can clone voices to sound nearly identical to the original speaker.
Although currently only available in preview, OpenAI has postponed the full release to strengthen societal defenses against realistic generative models.
The organization also called on companies to develop methods to trace the origin of audiovisual content and stressed the need to educate the public on how to identify misleading AI content.
Audio deepfakes in the contact center
OpenAI’s argument that it can learn to detect fraudulent AI content is a classic case of “easier said than done.” Thanks to the capabilities of its own technology, fraudsters are able to emulate voices with frightening accuracy.
In addition, these scammers try to deceive people using a variety of tactics.
Some of these tactics were revealed in a recent analysis by audio traffic monitoring expert Pindrop, which examined how audio deepfakes are being used to target call centers.
By examining a sample of spoofed calls, Pindrop was able to classify audio fraud cases into the following four patterns:
- Navigate IVR systems and steal basic account information
- Bypass IVR authentication
- Change account details
- Mimicking IVRs
The audio security company also provided advice on how call centers can protect themselves from this growing threat.
For more information on this, as well as more details on how malicious actors are targeting call centers, read the full article here.




